Talos Kubernetes - Post Install Details (Flux with Cloudflare)
About
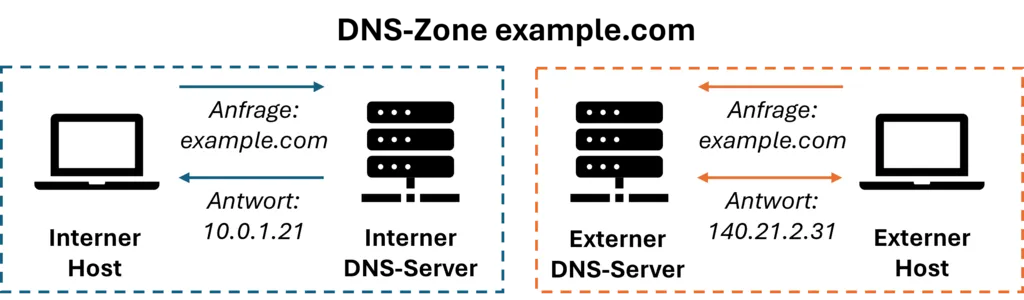
Cluster resources with internal addresses are routed via the internal nginx service, and likewise external addresses are routed via the external nginx service.
Applications with their ingress class set to internal will only be accessible to devices within the cluster,
whereas those with an external ingress class will be publicly available to anyone on the internet.
But what about when devices on your private network need to access an ‘internal’ resource, without being a part of the cluster?
A common example would be accessing Grafana dashboard metrics running internally at grafana.my.domain from your workstation.
This is exactly what Split DNS can accomplish.
Prerequisites
Initial Machine Setup for Talos Flux Cluster
Instructions
We will configure split DNS as mentioned in the post install instructions in github. To accomplish this in OPNsense, follow these steps:
- Go to Services > Unbound DNS > Query Forwarding
- Add new (select the ’+’ button)
- Ensure the box labeled ‘Enabled’ is checked.
- Enter your domain in the form of ‘my.doamin’. This should be the same value used during cluster config under
bootstrap_cloudflare.domaininconfig.yaml. - For IP address, use the IP of the
k8s_gatewayset in the cluster config. This is found underbootstrap_cloudflare.gateway_vipinconfig.yaml. - Optionally enter a description. I put ‘Split DNS’ to remind me why the rule is in place.
- Leave Port blank.
- Click save and then apply your changes. You may need to restart the Unbound DNS service.
- To test, run
dig gateway_vip hubble.your.domain, replacing gateway_vip with its associated value. If it returns the value ofbootstrap_cloudflare.ingressthen your internal nginx should assign an internal ip tohubble.your.domain. Check withkubectl get ingresses -A. You should see something like this:
NAMESPACE NAME CLASS HOSTS ADDRESS PORTS AGE
...
kube-system hubble-ui internal hubble.your.domain 192.168.1.20 80 1d
Next steps
Check out Talos Kubernetes - Add External Secrets to allow apps to securely pull secrets (api keys, tokens, etc.) with the added benefit of a cache to manage the pulls.
References
Onedr0p’s post install instructions in github
To learn more, read here: How to Configure Split DNS in OPNsense using Unbound DNS (homenetworkguy.com).